GRC's Password Haystack
Thoughts on passwords. I keep coming back to this article because passwords do not work. You need to do more, but more complex passwords are not the answer. This article was originally published on 08/2011 has been revisited on 2013.05, 2014.10, with changes throughout the text.
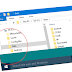
Gibson Research Company (GRC) wrote a fun password program, the "Password Haystack."
Link: https://www.grc.com/haystack.htm
In this program, type a password and it reports roughly how secure it is. (Note: GRC is a trustworthy site and I have full-faith in his honesty and security; you should feel safe about testing your passwords here.) Note this example password has a mixture of upper and lower-cased values, digits, but no special characters.
The site implies at 1,000 attempts per second, this password takes about 27 million years to hack. The trouble is -- this is for a brute-force password attack, which nobody uses. If they have the underlying database, such as a Rainbow table, or more commonly, a list of common passwords, they can hack millions of possibilities per second using relatively common equipment.
GRC goes on to suggest adding a 'special character', such as a predictable [space], adds one more digit to the length and theoretically changed the character set from 62 possible values to 95. According to GRC, the ubber-cluster now needs about 2 billion years to hack.

Fun to think about, but these calculations are not realistic. Adding a space (multiple-word passwords) does not change the number of characters from 62 to 95. The real count is 63 and the hackers know this.
Other Ideas
Straying from a brute-force attack, are there other ways to get a password? Of course, and these are even more fun. No matter how long, no matter how complex, no password is safe if you give it away through social engineering (fake login pages) or if the company is hacked (Adobe, for example) and all passwords are lost at the same time.
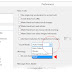
Passwords are hackable with this xkcd.com method:

20 Years of Password Nonsense
This now-famous xkcd comic describes the benefit of a simpler password, using multiple words, and it has circled the Earth about a million times:
But even this idea is flawed and is not as safe as the GRC site would suggest. Yes. Having a multi-word password, with spaces or not, is better than using "password123", but it is sadly prone to attacks, using some very sophisticated, but widely-available methods, described in a few moments.
And how many phrases (correcthorsebatterystaple) can you invent, for the myriad of places you need a password? You won't be able to keep them straight and will start to use the same password for each site -- but, as you already know, this is even more risky; a breach at one company is a breach in all.
What about Password Safes and Vaults?
Password Safes store your long, complicated, and numerous passwords in some other protected program or vault. Each time you need to login, you have to unlock the safe, find the account, and type the ugly password that you will never remember. In practice, this does not work and you will never use it.
Who wants to go to this trouble? And when all is said-and-done, this does not fix a password's biggest weakness.
It Gets Worse
How long do bute-force attacks take? Do they take longer with multi-word phrases? The real answer is it does not make that much of a difference. This amazing "arsTechnica" article discusses the techniques now being used. Be sure to glance through the hundreds of comments:
Article: Anatomy of a hack: How crackers ransack passwords like “qeadzcwrsfxv1331”
Link:
http://arstechnica.com/security/2013/05/how-crackers-make-minced-meat-out-of-your-passwords
Within a day or two, a single account can be de-coded, provided the credential database was stolen -- which happens too often.
The Real Weakness
No doubt, longer passwords slow the hackers down. But unless your personal account is a high-value target, such as a movie star or executive, it won't be hacked with brute force.
Instead, the most likely way to lose the password is when the company itself is hacked and all account credentials are lost at the same time. Any company worth its salt will have encrypted the password, but once the database is lost, they can brute-force-it at their leisure, using all the techniques described above.
In other words, your credentials will probably be stolen -- either by a database infiltration or by some social engineering scheme. A password, no matter how strong, is not enough to protect your stuff.
Of course you may say your stuff is not that important. Yes it is. Imagine getting on my machine -- with this account -- you could get to my Google Wallet and transfer money all over the place. Account information, contact lists, launch remote-controls to other computers, and other such mayhem. You could adjust my home thermostat.
Passwords will be lost.
Google 2-Step Authentication
What can you do? Password complexity is needed, but is ultimately a lost cause. No matter how good the password, when your credentials are lost by a database breach, it is nearly pointless. You need another layer of security and with this, you can use a simpler password scheme.
Consider my Gmail and Blogspot account. I have been using Google's 2-step authentication for several years. Each time I login, Google sends a text message to my phone (or now with a nifty app). Then, in a secondary login screen, I type a random numeric code that changes each time.
This works similarly to the RSA random-number dongles you used to see.
My login has become nearly impossible to hack.
Even if they have my account credentials, they can't login.
In practice, this is easy. Login to (Gmail), type your credentials. Three seconds later, type a six-digit numeric code. And now, with the new Google "Authenticator" app, I don't even have to wait the three seconds. Assuming my phone is secured, my logins are secured. Microsoft is now doing a similar process.
What if I loose my cell phone? Without going into details, Google has a moderately secure, alternate method for logging in. See this article for full details on the 2-step authentication.
See also this keyliner article: Using Google Authenticator
Password Recommendations:
With or without 2-step authentication, do these things for better password security:
1. Use a password phrase (two or more words). Each word should have mixed case, where the first letter is not capital, along with numbers or special characters. Do not end with a number.
2. Do not use these schemes:
First-letter-capitalized
Trailing digits
Dictionary words
Replace 1's with !'s, e's with 3's, s's with 5's
3. Use a different password for each site -- but use a scheme to help you remember.
The reason: If one password is compromised, you won't loose everything. But this admittedly makes passwords nearly impossible to remember. Consider this trick, which uses the same password on each site/program, but adds a suffix, making it unique.
For example:
If your normal password were "aB9dogglybarks"
use "aB9dogglybarks hotm" for your hotmail account.
use "aB9dogglybarks goog" for your google account
use "aB9dogglybarks bank" for your banking account
Devise your own scheme, then use it everywhere; make it predictable by you.
If the password were compromised, it would at least slow down automated programs from guessing the other accounts. Naturally, a human would see through this in a heart beat.
4. For dumb sites, where you could care-less if it were hacked, such as registration sites, Q&A forums, etc, use a single/same password (I call this an expendable or junk password), with moderate complexity. Do not use your password scheme.
5. When available, always use 2-step authentication.
If the 2-step vendor supports an app, use the app instead of SMS text messages (see Google, see Microsoft), because it is faster and easier.
What if your site does not allow passwords of this complexity? Typically, some sites limit you to 8-character passwords. Revolt. Write the admin and insist on the change. If enough people complain, they will switch.
Conclusions:
Passwords need to have some complexity, but don't go overboard because the very idea of a password is now a flawed design. Your only protection is some sort of two-factor authentication, which should be used whenever available. Unfortunately, we may end up with a dozen different styles, requiring a dozen different methods.
Related Articles:
Gmail Protection Steps
SMS Text Message: Your Gmail account has been hacked
Using Google Authenticator - a Google App
Google Documentation - 2 Step Authentication
Gibson Research Company (GRC) wrote a fun password program, the "Password Haystack."
Link: https://www.grc.com/haystack.htm
In this program, type a password and it reports roughly how secure it is. (Note: GRC is a trustworthy site and I have full-faith in his honesty and security; you should feel safe about testing your passwords here.) Note this example password has a mixture of upper and lower-cased values, digits, but no special characters.
The site implies at 1,000 attempts per second, this password takes about 27 million years to hack. The trouble is -- this is for a brute-force password attack, which nobody uses. If they have the underlying database, such as a Rainbow table, or more commonly, a list of common passwords, they can hack millions of possibilities per second using relatively common equipment.
GRC goes on to suggest adding a 'special character', such as a predictable [space], adds one more digit to the length and theoretically changed the character set from 62 possible values to 95. According to GRC, the ubber-cluster now needs about 2 billion years to hack.

Fun to think about, but these calculations are not realistic. Adding a space (multiple-word passwords) does not change the number of characters from 62 to 95. The real count is 63 and the hackers know this.
"Through 20 years of effort,
we have successfully trained everyone to use passwords that are hard for humans to remember,
but easy for computers to guess." -xkcd.com
we have successfully trained everyone to use passwords that are hard for humans to remember,
but easy for computers to guess." -xkcd.com
Other Ideas
Straying from a brute-force attack, are there other ways to get a password? Of course, and these are even more fun. No matter how long, no matter how complex, no password is safe if you give it away through social engineering (fake login pages) or if the company is hacked (Adobe, for example) and all passwords are lost at the same time.
Passwords are hackable with this xkcd.com method:

20 Years of Password Nonsense
This now-famous xkcd comic describes the benefit of a simpler password, using multiple words, and it has circled the Earth about a million times:
But even this idea is flawed and is not as safe as the GRC site would suggest. Yes. Having a multi-word password, with spaces or not, is better than using "password123", but it is sadly prone to attacks, using some very sophisticated, but widely-available methods, described in a few moments.
And how many phrases (correcthorsebatterystaple) can you invent, for the myriad of places you need a password? You won't be able to keep them straight and will start to use the same password for each site -- but, as you already know, this is even more risky; a breach at one company is a breach in all.
What about Password Safes and Vaults?
Password Safes store your long, complicated, and numerous passwords in some other protected program or vault. Each time you need to login, you have to unlock the safe, find the account, and type the ugly password that you will never remember. In practice, this does not work and you will never use it.
Who wants to go to this trouble? And when all is said-and-done, this does not fix a password's biggest weakness.
It Gets Worse
How long do bute-force attacks take? Do they take longer with multi-word phrases? The real answer is it does not make that much of a difference. This amazing "arsTechnica" article discusses the techniques now being used. Be sure to glance through the hundreds of comments:
Article: Anatomy of a hack: How crackers ransack passwords like “qeadzcwrsfxv1331”
Link:
http://arstechnica.com/security/2013/05/how-crackers-make-minced-meat-out-of-your-passwords
Within a day or two, a single account can be de-coded, provided the credential database was stolen -- which happens too often.
The Real Weakness
No doubt, longer passwords slow the hackers down. But unless your personal account is a high-value target, such as a movie star or executive, it won't be hacked with brute force.
Instead, the most likely way to lose the password is when the company itself is hacked and all account credentials are lost at the same time. Any company worth its salt will have encrypted the password, but once the database is lost, they can brute-force-it at their leisure, using all the techniques described above.
In other words, your credentials will probably be stolen -- either by a database infiltration or by some social engineering scheme. A password, no matter how strong, is not enough to protect your stuff.
Of course you may say your stuff is not that important. Yes it is. Imagine getting on my machine -- with this account -- you could get to my Google Wallet and transfer money all over the place. Account information, contact lists, launch remote-controls to other computers, and other such mayhem. You could adjust my home thermostat.
Passwords will be lost.
Google 2-Step Authentication
What can you do? Password complexity is needed, but is ultimately a lost cause. No matter how good the password, when your credentials are lost by a database breach, it is nearly pointless. You need another layer of security and with this, you can use a simpler password scheme.
Consider my Gmail and Blogspot account. I have been using Google's 2-step authentication for several years. Each time I login, Google sends a text message to my phone (or now with a nifty app). Then, in a secondary login screen, I type a random numeric code that changes each time.
This works similarly to the RSA random-number dongles you used to see.
My login has become nearly impossible to hack.
Even if they have my account credentials, they can't login.
In practice, this is easy. Login to (Gmail), type your credentials. Three seconds later, type a six-digit numeric code. And now, with the new Google "Authenticator" app, I don't even have to wait the three seconds. Assuming my phone is secured, my logins are secured. Microsoft is now doing a similar process.
What if I loose my cell phone? Without going into details, Google has a moderately secure, alternate method for logging in. See this article for full details on the 2-step authentication.
See also this keyliner article: Using Google Authenticator
Password Recommendations:
With or without 2-step authentication, do these things for better password security:
1. Use a password phrase (two or more words). Each word should have mixed case, where the first letter is not capital, along with numbers or special characters. Do not end with a number.
2. Do not use these schemes:
First-letter-capitalized
Trailing digits
Dictionary words
Replace 1's with !'s, e's with 3's, s's with 5's
3. Use a different password for each site -- but use a scheme to help you remember.
The reason: If one password is compromised, you won't loose everything. But this admittedly makes passwords nearly impossible to remember. Consider this trick, which uses the same password on each site/program, but adds a suffix, making it unique.
For example:
If your normal password were "aB9dogglybarks"
use "aB9dogglybarks hotm" for your hotmail account.
use "aB9dogglybarks goog" for your google account
use "aB9dogglybarks bank" for your banking account
Devise your own scheme, then use it everywhere; make it predictable by you.
If the password were compromised, it would at least slow down automated programs from guessing the other accounts. Naturally, a human would see through this in a heart beat.
4. For dumb sites, where you could care-less if it were hacked, such as registration sites, Q&A forums, etc, use a single/same password (I call this an expendable or junk password), with moderate complexity. Do not use your password scheme.
5. When available, always use 2-step authentication.
If the 2-step vendor supports an app, use the app instead of SMS text messages (see Google, see Microsoft), because it is faster and easier.
What if your site does not allow passwords of this complexity? Typically, some sites limit you to 8-character passwords. Revolt. Write the admin and insist on the change. If enough people complain, they will switch.
Conclusions:
Passwords need to have some complexity, but don't go overboard because the very idea of a password is now a flawed design. Your only protection is some sort of two-factor authentication, which should be used whenever available. Unfortunately, we may end up with a dozen different styles, requiring a dozen different methods.
Related Articles:
Gmail Protection Steps
SMS Text Message: Your Gmail account has been hacked
Using Google Authenticator - a Google App
Google Documentation - 2 Step Authentication
GRC's Password Haystack
 Reviewed by Unknown
on
10:21 PM
Rating:
Reviewed by Unknown
on
10:21 PM
Rating:
 Reviewed by Unknown
on
10:21 PM
Rating:
Reviewed by Unknown
on
10:21 PM
Rating:


















No comments: